[ad_1]
Machine studying (ML) on the edge requires highly effective edge requires highly effective edge gadgets with a novel set of necessities. The supply, security, and safety necessities for the sting differ from cloud since they’re positioned on the buyer web site, outdoors the information heart, and interface immediately with operational know-how (OT) and the web. Since edge places usually lack the bodily safety that information facilities have and lack the safety controls obtainable within the cloud, they’ve turn into engaging targets for unhealthy actors equivalent to cryptocurrency miners. In lots of circumstances, edge gadgets don’t have anti-malware defenses making it much more tough to detect cryptocurrency mining exercise.
An end-to-end safety mannequin that protects edge gadgets from hostile networks and protects delicate information and ML fashions is paramount for a profitable deployment. Clients can use AWS IoT Machine Defender to assist audit and monitor their edge system fleet. On this weblog submit, we present you the steps concerned in serving to to detect and mitigate cryptocurrency mining threats on edge gadgets utilizing AWS IoT Machine Defender {custom} metrics.
Cryptocurrency mining use case
Cryptocurrency, typically referred to as crypto-currency or crypto, is any type of forex that exists digitally or nearly and makes use of cryptography to safe transactions. Cryptocurrency mining is a course of of making new digital cash and is a compute intensive exercise that has been on the rise lately.
Cryptojacking is a kind of cybercrime that entails the unauthorized use of gadgets (edge computer systems, smartphones, tablets, and even servers) to mine for cryptocurrency and illicitly create forex. As cryptocurrency costs rise and extra highly effective edge gadgets with GPU capabilities are used to run ML on the edge use circumstances, there may be an growing risk of cryptojackers to use safety vulnerabilities on edge gadgets. When this occurs, edge computing assets are used to mine crypto forex leading to increased CPU/GPU utilization and a degradation in efficiency of edge purposes and a rise in ML on the edge inference processing occasions.
On this weblog, we present you easy methods to monitor CPU/GPU utilization and ML on the edge inference processing time with {custom} metrics that may assist point out crypto forex mining exercise on edge gadgets. AWS IoT Machine Defender {custom} metrics are metrics you outline which can be distinctive to your gadgets and use case. On this cryptocurrency mining cyber safety use case, you possibly can monitor for anomalies utilizing two {custom} metrics – CPU/GPU utilization metric and common ML on the edge inference time metric. Extra details about utilizing AWS IoT Machine Defender for detecting cryptocurrency mining might be discovered right here. Notice that to analyze an anomaly, it is advisable correlate the alarm particulars with different contextual info equivalent to system attributes, system metric historic traits, safety profile metric historic traits, commonplace metrics, and logs to find out if a safety risk is current.
Answer conditions
- AWS account
- A growth surroundings/pc with docker and AWS CLI put in.
- AWS function or consumer with capability to create a brand new IAM consumer or function for AWS IoT Greengrass minimal IAM coverage.
- A pc with the most recent browser.
- Fundamental understanding of Linux equivalent to creating directories, setting file permissions, and programming.
Answer structure and overview
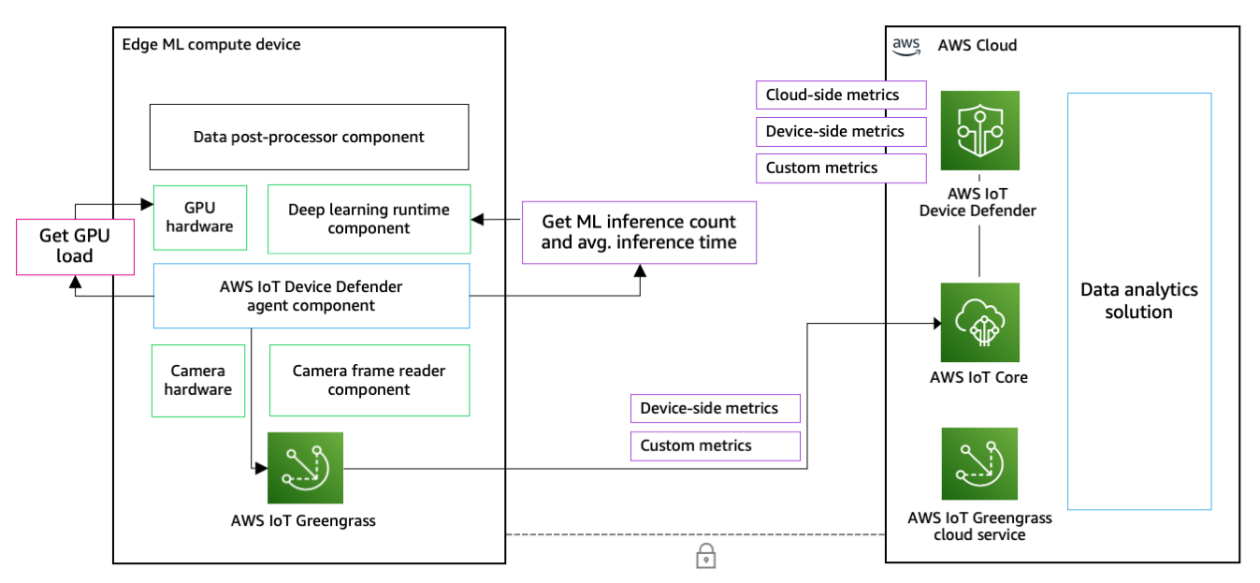
Our edge safety answer for detecting cryptocurrency mining threats implements edge software administration with AWS IoT Greengrass, {custom} metrics information assortment and ingestion to the cloud with AWS IoT Greengrass {custom} elements and AWS IoT Machine Defender for safety profile definition and monitoring.
The steps to implement the answer are as follows:
- Create an AWS IoT Greengrass system
- Create and deploy a {custom} AWS IoT Greengrass element for AWS IoT Machine Defender
- Outline safety profiles with {custom} metrics for GPU assets and common ML on the edge inference time in AWS IoT Machine Defender
- Simulate the GPU load and ML on the edge common inference time metric modifications for a cryptocurrency mining state of affairs
- Verify and acknowledge AWS IoT Machine Defender service’s alarm standing

Determine: Answer structure to assist monitor and detect edge gadgets for crypto forex mining threats
Answer stroll via
1. Put together and Publish AWS IoT Machine Defender element with {custom} metrics
Connect with your growth pc utilizing AWS CLI or AWS Cloud9 occasion. This weblog submit deploys the answer to the us-east-1 (N. Virginia) area by default. You’ll see directions to vary the area in case you need to deploy to a different area.
First, run the next to put in AWS IoT Greengrass Improvement Package to check and publish {custom} AWS IoT Greengrass elements.
python3 -m pip set up -U git+https://github.com/aws-greengrass/[email protected]We use a barely modified model of a public and open supply AWS IoT Machine Defender element for AWS IoT Greengrass. The modifications are primarily enhanced debugging/logging for simpler growth workflow and {custom} metrics definitions for simulated GPU useful resource metrics and ML on the edge inference time metrics.
The general public AWS IoT Machine Defender element is deployed from the central AWS IoT Greengrass element repository, however the modified model will probably be saved in your individual account.
Clone the Git repository of this weblog submit and run the element repository construct script:
cd ~/surroundings
git clone https://github.com/aws-samples/aws-iot-blogs-greengrass-device-defender-custom
cd aws-iot-blogs-greengrass-device-defender-custom
chmod +x construct.sh
./construct.sh
Run the next to construct and publish the AWS IoT Greengrass element. To vary the default area us-east-1, modify area part within the com.awsiotblog.DeviceDefenderCustom/gdk-config.json file.
gdk element construct
gdk element publish
Go to AWS IoT Greengrass console > Elements to substantiate your element is revealed.

2. Create and deploy a containerized AWS IoT Greengrass system
On this part, we’ll use docker containers to create an AWS IoT Greengrass system to simulate and characterize your edge system.
The Dockerfile within the repository will permit us to get the bottom AWS IoT Greengrass container picture and construct it with some GPU useful resource metric measurement information.
Run the next to construct the AWS IoT Greengrass system container.
cd ~/surroundings/aws-iot-blogs-greengrass-device-defender-custom
docker construct -t gg-awsiotblog-image .
The AWS IoT Greengrass container requires AWS credentials to provision these assets and deploy the native growth instruments. Create an IAM consumer with Minimal IAM coverage for installer to provision assets or retrieve non permanent AWS credentials from a task that has the identical minimal IAM coverage to supply it to the container. For particulars, see Run AWS IoT Greengrass in a Docker container with computerized useful resource provisioning.
Create a folder the place you place your credential file.
cd ~/surroundings/
mkdir ./greengrass-v2-credentials
Create a configuration file named credentials within the ./greengrass-v2-credentials folder. Add your AWS credentials to the credentials file within the following format.
[default]
aws_access_key_id = AKIAIOSFODNN7EXAMPLE
aws_secret_access_key = wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
aws_session_token = AQoEXAMPLEH4aoAH0gNCAPy...truncated...zrkuWJOgQs8IZZaIv2BXIa2R4Olgk
Embody aws_session_token for non permanent credentials solely.
Run the next to create, provision and initialize an AWS IoT Greengrass system. This container will characterize your edge system with GPU assets.
docker run -v $(pwd)/greengrass-v2-credentials:/root/.aws/:ro
-e GGC_ROOT_PATH=/greengrass/v2
-e AWS_REGION=us-east-1
-e PROVISION=true
-e THING_NAME=gg-awsiotblog-01
-e THING_GROUP_NAME=gg-awsiotblog
-e TES_ROLE_NAME=GGBlogTokenExchangeRole
-e TES_ROLE_ALIAS_NAME=GGBlogTokenExchangeRoleAlias
-e COMPONENT_DEFAULT_USER=ggc_user:ggc_group
--name gg-awsiotblog-01
gg-awsiotblog-image:newest
After working the docker container, you’ll see the ultimate log output as the next; this means your digital AWS IoT Greengrass system is provisioned and began efficiently.
…
Launching Nucleus…
Launched Nucleus efficiently..
NOTE: After creating the primary container, you possibly can run the command with completely different THING_NAME inputs to create extra digital edge gadgets.
You possibly can go to AWS IoT > Handle > Greengrass gadgets > Core gadgets to see the created AWS IoT Greengrass gadgets.

3. Deploy elements to the AWS IoT Greengrass simulated system fleet
Now, it’s time to deploy some elements to your newly created system, together with the {custom}/modified AWS IoT Machine Defender element.
Earlier than deploying the element, run the next command to permit the AWS IoT Greengrass system to obtain element artifacts from Amazon Easy Storage Service (Amazon S3).
cd ~/surroundings/
aws iam put-role-policy --role-name GGBlogTokenExchangeRole --policy-name GGComponentArtifactPolicy --policy-document file://component-artifact-policy.json
The deployed digital system is added into gg-awsiot-blog factor group. So, you’ll create a deployment that targets the gg-awsiot-blog factor group.
- Go to AWS IoT > Handle > Greengrass gadgets > Deployments
- Select Create, specify a deployment identify
- Choose the goal identify as gg-awsiotblog, select Subsequent
- On Step 2:
- Choose
com.awsiotblog.DeviceDefenderCustomunderneath My elements - Choose
aws.greengrass.Cliandaws.greengrass.Nucleusunderneath Public elements
- Choose
- On Step 3 – Configure elements, it is best to see your 3 chosen elements.
- Select “
com.awsiotblog.DeviceDefenderCustom” element and choose Configure element - On the proper pane, enter the next for Configuration to merge
{ "EnableGPUMetrics": true } - For the subsequent steps, proceed by deciding on Deploy.
After creating the deployment, your system will obtain the deployment, apply it and report the standing to the cloud. Lastly; you’ll see the Core gadgets part within the deployment particulars web page as your system reported as Wholesome.

Now, you could have your AWS IoT Greengrass system reporting device-side metrics and {custom} metrics to AWS IoT Machine Defender. You possibly can test the precise payloads that the element publishes.
docker exec -it gg-awsiotblog-01 grep "stdout. Publishing metrics:" /greengrass/v2/logs/com.awsiotblog.DeviceDefenderCustom.log
Copy and paste the output JSON to your favourite JSON parser/viewer to test the metrics revealed out of your gadgets.
4. Create a safety profile for {custom} GPU useful resource metric and common ML on the edge common inference time metric.
Firstly, you’ll begin with definition of the {custom} metrics in AWS IoT Machine Defender:
- Go to AWS IoT > Handle > Safety > Detect > Metrics and select Create.
- Create a {custom} metric for GPU load.
- For identify, specify
gpu_load_per_inference - For kind, select quantity.
- For identify, specify
- Create a {custom} metric for inference time.
- For identify, specify
avg_inference_time - For kind, select quantity.
- For identify, specify
Now, AWS IoT Machine Defender is ready to monitor two outlined {custom} metrics from the sting gadgets.
You possibly can proceed to create a safety profile that makes use of {custom} the GPU metric and the ML on the edge common inference time metric to guage the cryptocurrency risk state of affairs.
- Navigate to the Safety Profiles part of the AWS IoT Machine Defender Console: AWS IoT > Handle > Safety > Detect > Safety Profiles
- Select Create Safety Profile and select Create Rule-based anomaly Detect profile
- For Goal, select gg-awsiotblog
- Specify a Safety Profile identify
- Clear all Cloud-side metrics to maintain the main target.
- Choose two Machine-side {custom} metrics that you just simply created;
gpu_load_per_inferenceandavg_inference_time. - Select Subsequent
- Below the Outline metric behaviors part, specify the next parameters:
- Metric:
gpu_load_per_inference- Operator: “Much less Than”
- Worth: “40”
- Length: “5 minutes”
- Metric:
avg_inference_time- Operator: “Much less Than”
- Worth: “100”
- Length: “5 minutes”
- Metric:
- Select Subsequent
- Select Create

5. Run the cryptocurrency mining situation simulation
Now our simulated AWS IoT Greengrass system runs in a container and publishes system aspect metrics together with {custom} metrics to AWS IoT Machine Defender service. Present values of {custom} metrics are throughout the anticipated habits of the system.
In every container, there are two information that characterize {custom} metrics as /var/gpu_load_fb and /var/gpu_inference_fb; just like different obtainable system metrics like CPU temperature, load … and so forth. The {custom} AWS IoT Machine Defender element is configured to learn metric values from these information for every metric publish operation.
Now, you’ll replace the values in these information to simulate the situation of a cryptocurrency mining exercise in your GPU-powered system, alongside together with your ML mannequin. Improve of GPU load and common ML mannequin inference time will characterize this example as an abnormality.
docker exec -it gg-awsiotblog-01 bash -c "echo 85 > /var/gpu_load_fb; echo 180 > /var/gpu_inference_fb"
After working the replace, you possibly can test the revealed payloads for the system to see the growing {custom} metrics within the payload, utilizing the next command.
docker exec -it gg-awsiotblog-01 grep "stdout. Publishing metrics:" /greengrass/v2/logs/com.awsiotblog.DeviceDefenderCustom.log
As soon as metrics are delivered to the AWS IoT Machine Defender service and evaluated by the service, you’ll see the alarm standing on the Safety Profile web page.

Congrats! You made the AWS IoT Machine Defender service monitor and detect an irregular habits by configuring your edge system to ship GPU load and ML on the edge inference time {custom} metrics to assist detect cryptocurrency mining risk on the edge.
Lastly, be aware that we’ve created the safety profile with no automated actions. On this case, the alarm standing seems solely on the AWS IoT Machine Defender console and you’ll be able to begin a mitigation motion on the console. You may as well create and set an Amazon Easy Notification Service within the safety profile to inform customers or different companies and take personalized automated actions in case of an AWS IoT Machine Defender alarm. Verify the documentation for the AWS IOT Machine Defender Mitigation Actions for extra info.
Cleanup
- Cease and take away the docker container by working
docker cease gg-awsiotblog-01anddocker rm -v gg-awsiotblog-01instructions. - Delete the created AWS IoT Greengrass system.
- Delete the created {custom} AWS IoT Greengrass element.
- Delete the safety profiles and {custom} metrics in AWS IoT Machine Defender.
Conclusion
You will need to rapidly detect indicators of cryptocurrency mining exercise in your edge gadgets, as a way to defend your IoT/IIoT answer and preserve edge software efficiency. On this weblog submit, we demonstrated easy methods to outline {custom} metrics in AWS IoT Machine Defender to observe CPU/GPU utilization and common ML on the edge inference time to assist detect cryptocurrency mining actions by making a rule-based safety profile. Alternatively, prospects might use AWS IoT Machine Defender ML Detect to routinely set the safety profile with {custom} metrics. The answer might be prolonged through the use of this instance to create your individual {custom} metrics distinctive to your system fleet or use case, get alerts, and take mitigation actions utilizing AWS IoT Machine Defender. You possibly can examine different safety use circumstances which AWS IoT Machine Defender can help. Along with utilizing AWS IoT Machine Defender to audit and monitor your fleet of IoT gadgets, AWS recommends following the Ten safety golden guidelines for IIoT options, Implementing zero belief IoT options, Securing IoT with AWS whitepaper and AWS IoT Lens and being alert to the most recent cryptojacking traits.
In regards to the authors
 Emir Ayar is a Tech Lead Options Architect on the AWS Prototyping workforce. He makes a speciality of serving to prospects construct IoT, ML on the Edge, and Trade 4.0 options and implement architectural finest practices. He lives in Luxembourg and enjoys taking part in synthesizers. Emir Ayar is a Tech Lead Options Architect on the AWS Prototyping workforce. He makes a speciality of serving to prospects construct IoT, ML on the Edge, and Trade 4.0 options and implement architectural finest practices. He lives in Luxembourg and enjoys taking part in synthesizers. |
 Ryan Dsouza is a Principal Options Architect for IoT at AWS. Primarily based in New York Metropolis, Ryan helps prospects design, develop, and function safer, scalable, and progressive options utilizing the breadth and depth of AWS capabilities to ship measurable enterprise outcomes. Ryan has over 25 years of expertise in digital platforms, good manufacturing, vitality administration, constructing and industrial automation, and OT/IIoT safety throughout a various vary of industries. Earlier than AWS, Ryan labored for Accenture, SIEMENS, Normal Electrical, IBM, and AECOM, serving prospects for his or her digital transformation initiatives. Ryan Dsouza is a Principal Options Architect for IoT at AWS. Primarily based in New York Metropolis, Ryan helps prospects design, develop, and function safer, scalable, and progressive options utilizing the breadth and depth of AWS capabilities to ship measurable enterprise outcomes. Ryan has over 25 years of expertise in digital platforms, good manufacturing, vitality administration, constructing and industrial automation, and OT/IIoT safety throughout a various vary of industries. Earlier than AWS, Ryan labored for Accenture, SIEMENS, Normal Electrical, IBM, and AECOM, serving prospects for his or her digital transformation initiatives. |
[ad_2]